Passwordless SSH login to remote servers is convenient for interactive users and often essential for automated tasks. However, when the remote system uses Kerberos-authenticated storage, as is the case for both DartFS (and AFS), the common method of key pairs does not work. The problem is that a key pair is considered acceptable authentication for login, but carries no authentication for the file server which holds the home directory and data shares. The symptom is a partially successful login, but "permission denied" on all attempts to read files in your home directory or any data share.
The solution is the software framework called GSSAPI (Generic Security Services Application Programming Interface). The idea is that you authenticate on the client - typically the machine you are sitting at, and then SSH (or SFTP, SCP, SMB mount or other GSSAPI-enabled service) will pass your credential to the remote system, where it is checked and then used to log you in. There are two features which must be enabled in any client program - which may be command line options, configuration file settings or preference menu settings, depending on the software. They usually have the same names as the directives used in OpenSSH, described below. On a domain-joined Windows system, you have authenticated by logging in to Windows, and GSSAPI-enabled software will use that credential automatically.
Supported clients (partial list)
- Mac command line ssh, sftp, scp (see caveats below)
- Mac Fetch SFTP client
- Linux command line ssh, scp, sftp
- Windows MobaXterm ssh in local terminals
Unsupported clients
- Windows MobaXterm prior to v20
- Unfortunately MobaXterm enables GSSAPIAuthentication by default, but older releases have no support for GSSAPIDelegateCredentials. This makes it confusing.
- Windows 10 Microsoft-supplied command line SSH
- Windows SSH Secure Shell (ssh.com, legacy free client)
Partially Supported
Windows clients support login via GSSAPI, but do not trust credential passing for filesystem access. This greatly limits the usefulness.
- Windows PuTTY ssh client
- Windows Tectia (ssh.com commercial offering)
- Windows MobaXterm v20 or later.
- Windows 11 Microsoft-supplied command line SSH (see caveat below)
Note that if a client private key exists, it will be checked first, before considering GSSAPI or prompting for a password. It may be necessary to use SSH client options to prevent use of keys with servers which cannot use them, while retaining them for other servers.
Remote servers must also be prepared to use GSSAPI, by registering with the authentication server and storing a key which can be used to validate the credentials passed to them. For services using active directory tickets (Dartmouth NetID), the common term for this is 'joining to the domain'. For Windows clients to work, an Active Directory property must also be set for the server.
Client configuration details
Linux and Mac OpenSSH
You must obtain a credential first, using "kinit", before running ssh. The ssh command line option "-K" can be used, or both of the following directives placed in the configuration file (~/.ssh/config):
GSSAPIAuthentication yes
This enables presenting the credential to the remote server to be used as authentication
GSSAPIDelegateCredentials yes
This enables passing a copy of the credential to the remote server to be used for subsequent access to other services - most commonly filesystem access.
Caveats for MacOS:
- You must authenticate with your NetID explicitly, before running SSH. You can use the command line kinit program, or Ticket Viewer.app
- e.g. kinit netid@KIEWIT.DARTMOUTH.EDU
- substitute your NetID, and give your password at the prompt.
- The SSH client supplied with MacOS (at least through MacOS 15) strips the 'renewable' property from your credential before passing it to the remote server. This means that it will expire at the same time as the original credential on your Mac, and cannot be extended by running krenew. This limits the usefulness to short jobs, and in particular it cannot usefully be used to submit jobs to the Discovery scheduler.
- MacOS (at least up through MacOS 15) creates a session key with a deprecated encryption type. You will be logged in to the remote server, but on newer servers, unable to see DartFS. The fix is to edit a local configuration on the Mac, to tell it to use only the newer encryption. You can download the attached krb5.conf file and install it into /etc/krb5.conf. This also sets the default authentication domain, so you do not need to specify @KIEWIT.DARTMOUTH.EDU
Caveat for Windows:
- The command line SSH program requires that you use:
- the -K option to tell it to pass your credential to the remote server
- the real hostname of the remote server, not an alias. Most of the Research Computing servers are commonly known by aliases.
Alias to Hostname Mappings
| Alias |
Hostname |
| discovery.dartmouth.edu |
slurm-fe01-prd.dartmouth.edu |
| andes.dartmouth.edu |
andes8.dartmouth.edu |
| polaris.dartmouth.edu |
polaris8.dartmouth.edu |
- The MobaXterm, PuTTY and WinSCP programs are able to use hostname aliases.
- Optionally, you can eliminate the need for the -K flag in the SSH command and/or define aliases for the real hostnames by placing appropriate SSH configuration commands in a text file named config and placing the config file in a subdirectory named .ssh in your Windows user home directory. An example config file is:
Sample config File
|
Host *
GSSAPIAuthentication yes
GSSAPIDelegateCredentials yes
Host discovery discovery.dartmouth.edu
HostName slurm-fe01-prd.dartmouth.edu
Host andes andes.dartmouth.edu
HostName andes8.dartmouth.edu
Host polaris polaris.dartmouth.edu
HostName polaris8.dartmouth.edu
|
Windows PuTTY (domain-joined client)
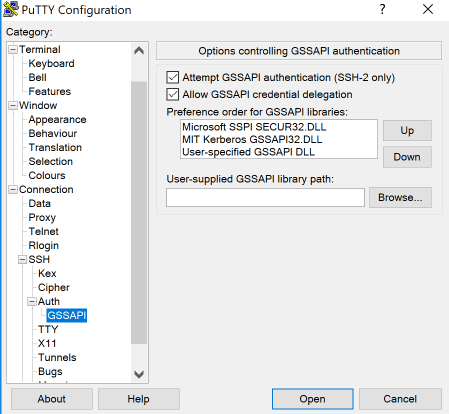
- In the configuration menus, select Connection: SSH: Auth: GSSAPI
- Check "Attempt GSSAPI authentication"
- Check Allow "GSSAPI credential delegation"
- In the configuration menus, select Connection: Data
- Put your NetID into "Auto-login username", or check the "Use system username" for a domain-joined system.
- Save the configuration
Windows MobaXterm (domain-joined client)
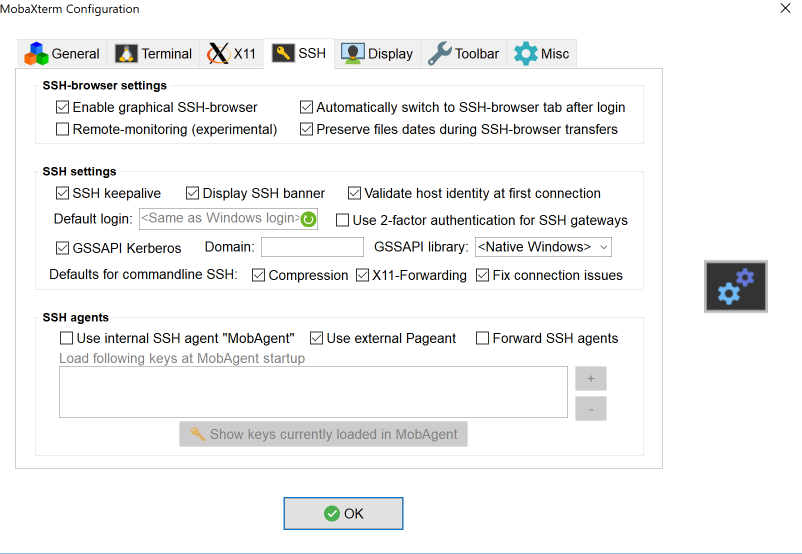
- In the Settings menus for all sessions, select SSH
- Check the box GSSAPI Kerberos
- Select OK
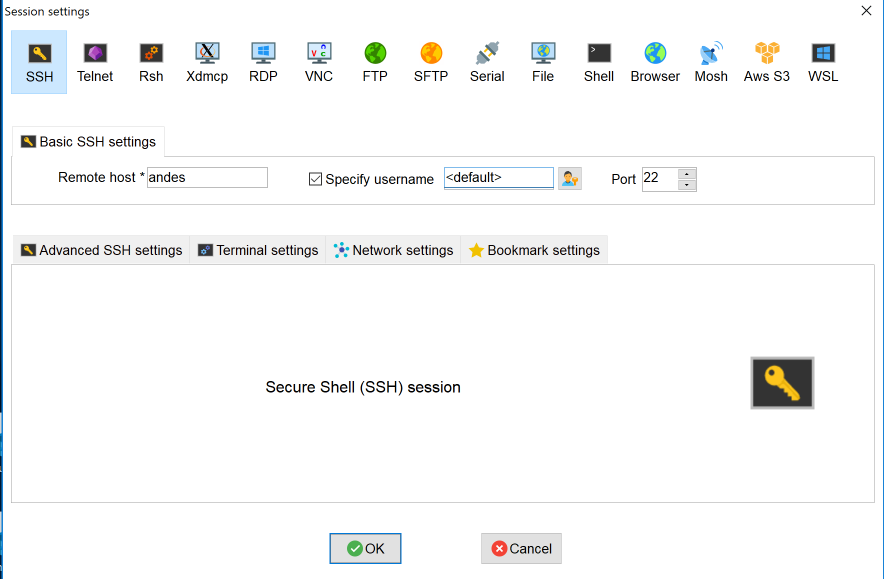
- When setting up a particular SSH session, check Specify username and enter your NetID or leave it as <default> for a domain-joined system.
- Select OK
Non-domain-joined Windows clients
It is possible to use passwordless logins using PuTTY or MobaXterm on systems where you do not use your NetID for login (non-domain-joined). However, you need to install some additional software to enable you to authenticate to the Dartmouth Active Directory manually. Please contact Research.Computing for assistance. This will be described in a future article.