Body
Digital hygiene, self-care in the digital realm, involves a series of practices and habits aimed at safeguarding and enhancing one's digital well-being. Much like self-care routines contribute to physical and mental health, digital hygiene focuses on maintaining the health, security, and overall well-being of our digital lives.
Protect Personal Information
Protecting your personal information is a crucial aspect of digital hygiene, focusing on safeguarding one's private data in the digital realm. This practice involves being judicious about the information you share online, including personal details like your address, phone number, and financial information. It's like setting boundaries in personal interactions, but in the digital space.
Strengthen Online Privacy Settings
- Review Social Media Settings
- Regularly adjust privacy settings on social media, limiting public sharing of personal details like address, phone number, and email.
- Check Resumes and CVs
- Ensure resumes or CVs posted online don't contain sensitive information. It's common practice for students to use their educational email addresses for professional purposes. However, it's important to use discretion and ensure other sensitive information (like home addresses, phone numbers, date of birth, or social security number) is not included alongside your email address on these documents.
- Broaden the Scope Beyond Social Media
- Include cloud storage, shopping sites, and other platforms where personal behavior or preferences could be exposed.
- Remove Contact Information from Public Directories
- Note: current students may request that Dartmouth directory information not be released without their prior consent. The request for a confidentiality hold must be made in writing, with a student's signature, to: the Registrar of Geisel, Guarini, Thayer, or Tuck, or the Undergraduate Deans Office for students enrolled in the College. For more information, please see https://student-affairs.dartmouth.edu/policy/dartmouth-institutional-ferpa-policy
- Adjusting Privacy Settings on common platforms
Click Here - For Platform Specific Instructions
Facebook
Meta privacy policy
Facebook's Privacy Settings
Step 1: Access Privacy Settings
- Desktop
- Click on the downward-facing arrow in the top-right corner, then select "Settings & Privacy" > "Settings."
- Mobile
- Tap the hamburger menu (three horizontal lines), scroll down, and tap on "Settings & Privacy" > "Settings."
Step 2: Adjust Privacy Settings
- Privacy Checkup: Facebook offers a Privacy Checkup that guides you through important settings. Start here.
- Profile Privacy: Control who can see your posts, limit who can see your future posts, and review who can tag you.
- Timeline and Tagging: Manage who can post on your timeline, review posts you're tagged in before they appear, and control who can see tagged content.
- Location: Adjust who can see your location and disable location history.
- Apps and Websites: Review and remove third-party apps that have access to your data.
- Ads: Tailor ad preferences, disable ad personalization, and manage ad settings.
Step 3: Additional Settings
- Security and Login: Enable two-factor authentication for extra security.
- Blocking: Manage blocked users, app invites, and event invites.
- Public Posts: Double-check past public posts and adjust their privacy settings if needed.
Step 4: Regularly Review Settings
- Stay Updated: Facebook occasionally updates its privacy settings. Periodically revisit and adjust settings based on your preferences.
- Activity Log: Review your activity log to see what's visible to others and adjust settings if needed.
Instagram
Meta privacy policy
Instagram privacy settings
Step 1: Access Privacy Settings
- Open Instagram App: Tap your profile picture in the bottom right to go to your profile.
- Go to Settings: Tap the three horizontal lines in the top-right corner (on iOS) or the three horizontal lines at the bottom (on Android) and select "Settings."
Step 2: Adjust Privacy Settings
- Account Privacy: Select "Privacy" > "Account Privacy" to set your account to private, controlling who can see your posts.
- Story Privacy: Manage who can reply to your stories and who can see your story content.
- Comments: Filter and block comments to control what's visible on your posts.
- Tags: Control who can tag you in photos and who can see posts you're tagged in.
- Activity Status: Disable if you don’t want others to see when you were last active.
- Restricted Accounts: Restrict accounts to limit their interactions with you without outright blocking them.
Step 3: Additional Settings
- Two-Factor Authentication: Enable for added security in "Security" settings.
- Manage Followers: Review and remove followers or block accounts.
- Data Usage: Manage data sharing with third-party apps.
- Story Sharing: Customize who can share your stories.
- Sensitive Content Control: Control how much sensitive content you see.
Step 4: Regularly Review Settings
- Stay Updated: Instagram updates its settings periodically, so revisit your privacy settings regularly.
- Activity Log: Review your activity log to see what's visible to others and adjust settings if needed.
TikTok
TikTok's Privacy policy
TikTok's Privacy settings
Step 1: Access Privacy Settings
- Open TikTok App: Launch the TikTok app on your mobile device.
- Go to Profile: Tap the "Me" icon at the bottom right to access your profile.
Step 2: Adjust Privacy Settings
- Privacy and Safety: Tap the three dots or the three lines in the top right corner (iOS/Android respectively) to access Settings. Then tap "Privacy and Safety."
- Account Privacy: Set your account to private to approve followers before they can see your content.
- Comments: Control who can comment on your videos and filter comments.
- Duets and Reactions: Manage who can create duets with you and who can react to your videos.
- Who Can Download Your Videos: Choose who can download your videos (Everyone, Friends, or Off).
Step 3: Additional Settings
- Block Users: In "Privacy and Safety," manage and block users you don't want interacting with you.
- Restricted Mode: Enable this mode to limit the appearance of content that may not be appropriate for all audiences.
- Allow List: Control who can interact with you and view your content.
- Data and Privacy: Review and manage data sharing settings within the "Data and Privacy" section.
- Two-Factor Authentication: Enable for added account security if available in your region.
Step 4: Regularly Review Settings
- Stay Updated: TikTok often updates its settings. Periodically check for updates and adjust settings as needed.
- Activity Log: Review your activity log to see interactions and adjust settings if necessary.
X (Formerly Twitter)
X's (Twitter's) Privacy policy
X's (Twitter's) Privacy settings
Step 1: Accessing Privacy Settings
- Open Twitter: Log in to your Twitter account via the web or the Twitter app.
- Access Settings: Click on your profile picture in the top right corner and select "Settings and privacy."
Step 2: Adjust Privacy Settings
- Privacy and Safety: Click on "Privacy and safety" to access key settings.
- Tweet Privacy: Adjust who can see your tweets—either "Public" (everyone) or "Protected" (only approved followers).
- Photo Tagging and Location: Manage who can tag you in photos and see your location information.
- Direct Messages: Control who can send you direct messages—either everyone or only those you follow.
- Tweet Sharing: Toggle off options like "Share your data with Twitter's business partners" if preferred.
- Tweet and Account Discoverability: Decide if you want your account to be discoverable by email or phone number.
Step 3: Additional Settings
- Muted Words and Accounts: Use the mute feature to silence specific words, phrases, or accounts.
- Blocked Accounts: Review and manage blocked accounts in the "Privacy and safety" section.
- Sensitive Content: Adjust settings for viewing sensitive content.
- Two-Factor Authentication: Enable this for an extra layer of security under the "Account" settings.
Step 4: Regularly Review Settings
- Stay Updated: Keep an eye out for any new privacy features or updates Twitter might roll out.
- Review and Adjust: Periodically review your settings and make adjustments according to your preferences or changes in Twitter's interface.
Bing (Microsoft) Search
Bing Privacy policy
Bing Privacy settings
Bing Search doesn't have extensive user-specific privacy settings as it operates more as a search engine. However, you can take some general steps to enhance your privacy:
Step 1: Browser Settings
- Use Private Browsing: Consider using your browser's private or incognito mode to prevent the storage of search history and cookies.
Step 2: Microsoft Account Settings
- Microsoft Privacy Dashboard: If you have a Microsoft account connected to Bing, visit the Microsoft Privacy Dashboard (https://account.microsoft.com/privacy/) to review and manage privacy settings related to your Microsoft account.
Step 3: Browser Extensions
- Privacy-Focused Extensions: Install browser extensions or add-ons that enhance privacy, such as ad blockers, tracking blockers, and script blockers.
Step 4: Review Bing Policies
- Bing Privacy Policy: Familiarize yourself with Bing's privacy policy (https://privacy.microsoft.com/en-us/privacystatement) to understand how your data is handled during searches.
Google Search
Google's Privacy policy
Google's Privacy settings
Step 1: Google Account Settings
- Sign In: Log in to your Google account.
- Go to Account Settings: Click on your profile picture at the top right and select "Manage your Google Account."
Step 2: Adjust Privacy Settings
- Web & App Activity: Click on "Data & personalization" and review your Web & App Activity settings. You can pause it or auto-delete activity after a certain period.
- Location History: Similarly, manage your Location History settings to disable or auto-delete location data.
- Ad Personalization: Under "Ad personalization," control how ads are personalized based on your activity.
Step 3: Google Search Settings
- Search Settings: Go to the Google homepage and click on "Settings" at the bottom right.
- Search Settings on Web: Adjust SafeSearch to filter explicit content if needed.
- Search History: Access "My Activity" (available in the Google Account settings) to review and delete your search history.
Step 4: Browser Settings
- Incognito Mode: Use your browser's incognito or private mode to prevent storing search history.
- Privacy Extensions: Consider installing privacy-focused browser extensions to block trackers and enhance anonymity.
Step 5: Review Google's Policies
- Privacy Policy: Familiarize yourself with Google's privacy policy (https://policies.google.com/privacy) to understand how your data is used.
Reddit
Reddit's Privacy policy
Reddit's Privacy settings
Step 1: Accessing Preferences
- Log In: Sign in to your Reddit account.
- User Settings: Click on your profile icon in the top-right corner and select "User Settings."
Step 2: Adjust Privacy Settings
- Profile Information: Under "Profile," choose what information is visible on your profile (bio, posts, comments).
- Personalization: Adjust content recommendations and personalization settings under "Personalization Preferences."
- Messages: In "Messaging Preferences," control who can send you private messages and chat requests.
Step 3: Security and Privacy
- Password and Email: Ensure your password and email are secure and up-to-date under "Password/email."
- Third-Party App Authorization: Check and remove any unauthorized third-party apps in "Authorized Apps."
- Blocked Users: Manage and review blocked users in "Blocked."
Step 4: Notification Settings
- Notification Settings: Customize what notifications you receive and how often under "Notifications."
- Email Notifications: Adjust email notification preferences to control what notifications are sent to your email.
Step 5: Review Reddit's Policies
- Privacy Policy: Familiarize yourself with Reddit's privacy policy (https://www.redditinc.com/policies/privacy-policy) to understand how your data is handled.
4Chan
4Chan's Privacy policy / rules
Privacy settings NONE
Anonymity:
- No Accounts: 4chan doesn’t require user accounts. Posts are anonymous by default, identified only by a generated string of characters.
- Avoid Personal Information: Refrain from sharing any identifiable information in your posts.
Post Deletion:
- No Post Editing: Once a post is submitted, it cannot be edited. Consider this before posting.
- Post Deletion: Posts on 4chan are temporary and will be deleted after a certain period or after the thread reaches the post limit. Be mindful that you cannot manually delete your posts.
Browsing:
- Use Caution: Due to the anonymous nature of the platform, exercise caution while browsing and interacting with content.
- No Tracking: 4chan doesn’t track users through accounts or cookies, but your IP address may be logged.
Community Guidelines:
- Abide by Rules: Follow 4chan’s rules and guidelines for posting. Each board has specific rules that users are expected to adhere to.
Privacy Tools:
- Use VPNs: Consider using a Virtual Private Network (VPN) to obscure your IP address while browsing.
- Be Cautious with Online Sharing:
- Think Before Posting: Carefully consider what personal information you reveal in posts, especially backgrounds in photos and details in public forums and profiles.
- Avoid oversharing: Be particularly wary of sharing your schedule, location, extended absences, and responses to trending social media posts that probe for personal details.
- Beware of Scams:
- Recognize Deceptive Tactics: Stay alert to attempts at phishing or unsolicited offers that may be too good to be true.
- Email Vigilance: Exercise caution with email attachments and offers, understanding that legitimate entities won't ask for sensitive information via email.
- Practice Safe Browsing:
- Identify Secure Websites: Look for 'https' in URLs and verify the legitimacy of websites before sharing personal information.
- Avoid Malicious Sites: Stay clear of suspicious websites that might steal data.
- Reputable Site Engagement: Only share personal data with well-established, reputable sites.
- Consider Impact of Forum Participation: Be aware of potential repercussions from engaging in online forums.
-
Click Here - For More Safe Browsing Tips
- Check the URL: Look at the website's URL. Make sure it starts with "https://" rather than just "http://". The "s" stands for secure and indicates that the website encrypts data transmitted between your browser and the site, making it harder for hackers to intercept.
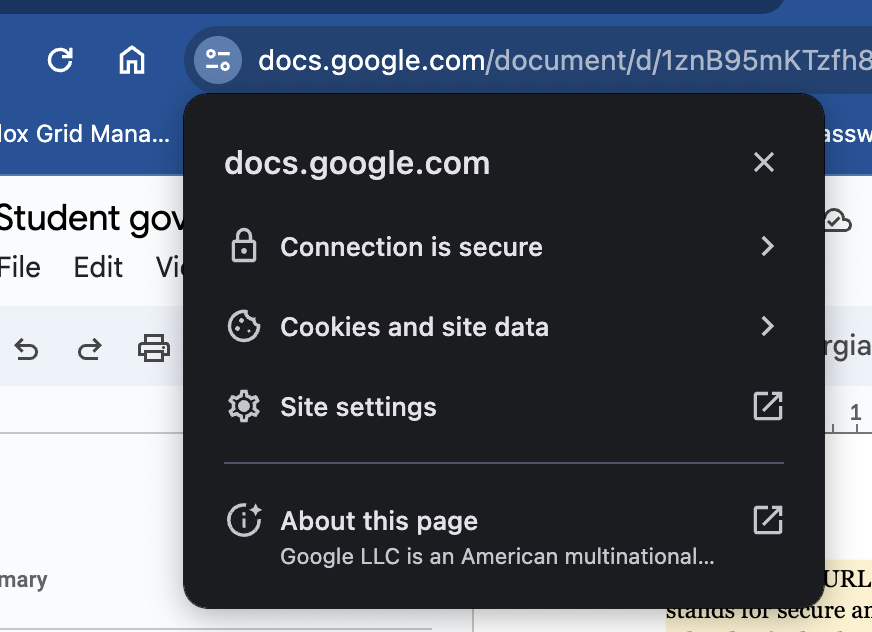
- Look for a Padlock: or look for the double line right before your URL in Chrome. See screenshot above. Check for a padlock icon next to the URL in the address bar. This indicates a secure connection. Click on the padlock to view the site's security details.
- Check Website Reputation: Use online tools or services that evaluate website safety. Services like Google Safe Browsing or Norton Safe Web can help determine if a site has been flagged for phishing or malware.
- Google website transparency report and instructions: https://transparencyreport.google.com/safe-browsing/search?hl=en
- https://www.virustotal.com/gui/home/url
- Read Reviews and Check Ratings: Look for reviews or ratings of the website on reputable platforms. Other users' experiences can provide insights into the site's reliability.
- Verify Contact Information: Legitimate websites usually have clear contact information, including an address, phone number, and email. Absence of such information might indicate a potential issue.
- Be Wary of Suspicious Links: Avoid clicking on links from unsolicited emails, messages, or unfamiliar websites. These links can lead to phishing sites or malware downloads.
- Consider Using an Alias:
- Minimize Digital Footprints: When signing up on new or sensitive sites, contemplate using an alias to protect your interests and privacy.
- Review Your Digital Footprint:
- Audit Social Media and Online Profiles: Periodically check and clean up old posts and profiles.
- Protect Domain Registration Info: If you own a website, ensure WHOIS information is private.
- WHOIS is a protocol used to query databases for information on the registration of domain names and IP addresses. To keep WHOIS information private and protect personal details from being publicly accessible, many domain registrars offer a privacy service or WHOIS privacy protection. This service replaces your personal information in the WHOIS database with the information of a forwarding service (done by the registrar) or a proxy, thereby keeping your personal details confidential. To ensure your WHOIS information is private, you should opt for these privacy services when registering or managing your domain through your domain registrar's website. Please contact your domain registrar for more information.
- Stay Informed of Data Breaches: Sign up for breach notifications and monitor how your data is shared online (see "Protect Your Accounts").
- Set Up Alerts:
Click Here - On How To Setup Alerts
Bing (Microsoft) Search
You can track mentions of your name on Bing with an RSS reader using these steps:
Create a Bing Search Result Alert
- Visit Bing: Go to [Bing.com](https://www.bing.com/) on your web browser.
- Search Your Name: Enter your name in the search bar and press Enter to perform a search.
- Set Up RSS Feed: If you're interested in tracking the search results for your name regularly, look for the "Feed" option (usually found at the bottom of the search results page) and click on it.
- Add to RSS Reader: Copy the URL provided for the RSS feed and add it to your RSS reader or a feed aggregator. This won't provide notifications but will help you track changes in search results over time.
Regular Manual Checks
- Manually Search on Bing: Periodically perform manual searches of your name on Bing to review the search results and see if there are any new mentions.
Google Search
Google Alerts
- Set Up Google Alerts: Go to [Google Alerts](https://www.google.com/alerts) and sign in with your Google account.
- Create a New Alert: In the search bar, enter your name (in quotes for exact matches) as the alert query.
- Customize Settings: Adjust settings like how often you want to receive alerts, sources (everything, news, blogs, etc.), language, region, and notification preferences.
- Save the Alert: Click on "Create Alert" to save your alert settings.
Check Google Search
- Manual Search: Periodically, perform manual searches of your name on Google. Simply enter your name in the search bar and review the results.
Review Social Media and Websites
- Check Social Media: Visit social media platforms where you have accounts and search for your name there.
- Monitor Personal Websites/Blogs: If you have a personal website or blog, check if your name appears in search results for those sites.
Protect your accounts
Protecting your accounts is a critical component of digital hygiene, emphasizing the need to secure your online accounts to safeguard against cyber threats These steps are vital in preventing unauthorized access, protecting against potential risks such as hacking, identity theft, and data breaches.
- Use Strong and Unique Passwords for Each Account:
- Password-Protect Your Computers and Devices:
- Ensure all your personal devices are secured with strong passwords.
- Leverage Built-in 'Strong Password' Features:
- Before utilizing a password manager, it's essential to secure your device and linked accounts (like Apple or Google) with multi-factor authentication (MFA) and strong passwords, as these credentials, if compromised, could give attackers access to all your stored passwords, posing a significant security risk.
- Windows: The Windows Security settings offer recommendations for creating strong passwords and can integrate with Microsoft Edge to manage and suggest complex passwords for online accounts.
- macOS: Apple's Keychain Access provides a password management system that suggests strong, unique passwords for websites and apps, which are then stored securely in the iCloud Keychain.
- iOS: Similar to macOS, iOS suggests strong passwords for websites and apps, stored securely and accessible across devices via iCloud Keychain.
- Android: Google's Password Manager integrated into Android suggests strong passwords when you sign up for new accounts or change passwords, storing them securely in your Google account for easy access across devices.
- Avoid Password Reuse:
- Using different passwords for each service prevents a breach on one account from compromising others.
- A motivated attacker can link you to other accounts if you use the same password elsewhere.
- It's common for attackers to try stolen credentials on multiple platforms.
- Stay Alert for Breach Notifications:
- Monitor for alerts that your password or personal information has been compromised.
- Have I Been Pwned? (HIBP) is a widely recognized website that allows users to check if their personal information has been compromised in data breaches. While Dartmouth does not officially endorse third-party sites, HIBP is a trusted resource for monitoring potential data exposures.
- Go to https://haveibeenpwned.com/
- Click on Notify Me
- Enter the email address you wish to be notified about
- The site will now notify you of any new breaches that email shows up in.
- Enable (Multi) Two-Factor Authentication (2FA/MFA)
- Activate MFA on All Critical Accounts: Prioritize enabling MFA on accounts that hold sensitive data, like email, banking, social media, and work-related platforms.
- Use Authenticator Apps When Possible: Opt for authenticator apps over SMS codes for MFA, as they provide better security and are less susceptible to interception and work when you do not have the best reception.
- Keep Backup Codes Secure: When setting up MFA, most platforms provide backup codes. Store these codes in a secure location, separate from your device, in case you lose access to your primary MFA method.
- Regularly Update Your Recovery Information: Ensure your account recovery information (like phone numbers or backup emails) is up-to-date to prevent lockouts. Remember to consider this step when getting a new phone!
Protect your devices
Protecting your devices is a vital element of digital hygiene, focusing on safeguarding the physical and software integrity of your digital tools. The importance lies in the fact that these devices are gateways to your personal and professional life, storing a wealth of sensitive information. Protecting them involves implementing security measures like password protection, encryption, and regular software updates. Additionally, it includes physical care, like not leaving devices unattended and protecting them from damage.
- Password Protect All Devices:
- Set strong passwords for all your devices, including smartphones, tablets, and computers. This is the first and most basic line of defense.
- Encrypt Your Device:
- Ensure your device data is encrypted. This adds an extra layer of security, making it difficult for unauthorized persons to access your information if your device is lost or stolen.
- How to encrypt your device
- Mac: Use FileVault to encrypt your entire system. It's available in the Security & Privacy settings.
- Windows: BitLocker is the built-in encryption feature. Access it through Control Panel > System and Security > BitLocker Drive Encryption.
- iOS: Encryption is enabled by default when you set a passcode on your iPhone or iPad.
- Android: Go to Settings > Security > Encrypt Phone to start the encryption process
- Shred or Securely Delete Sensitive Materials
- For Windows
- For macOS
- Since macOS 10.11, macOS no longer offers a native secure erase function, you can manage file deletion securely by enabling encryption.This ensures that even if files are recovered, they cannot be accessed without decryption. (See "Encrypt Your Device")
- Consider using Permanent Erase
- For advanced users, the
rm -p command in Terminal offers a manual deletion method. Always back up important data before proceeding with these methods to prevent accidental loss.
- Physical Security Awareness:
- Avoid Leaving Devices Unattended: Always keep your devices with you or in a secure location.
- Be Aware of Your Surroundings: Be cautious when using your devices in public spaces.
- Secure Paper Documents: Alongside digital data, ensure any physical documents with sensitive information are also kept secure.
- Shred or Securely Delete Sensitive Materials:
- When disposing of documents or digital files with personal information, use a shredder or secure delete software to prevent recovery.
- Software Protection:
- Install Device Protection Software/Antivirus: Protect your devices from malware and viruses.
- Keep Software Up to Date: Regularly update your device's operating system and applications to patch security vulnerabilities.
- Regular Data Backups: Consistently back up important data from your devices. This ensures you have a recovery option in case of data loss.
- Use Secure Networks:
- Avoid Public Wi-Fi for Sensitive Tasks: Public networks can be insecure. Use a VPN (Virtual Private Network) for a safer connection.
- Secure Your Home Wi-Fi Network: Ensure your home Wi-Fi has a strong password and updated security settings.
For more help with this process
Please don’t hesitate to call our Client Technology Consulting team at (603) 646-2999 | toll-free 1-855-764-2485 or email help@dartmouth.edu for help.
The information provided in these guidelines does not, and is not intended to, constitute legal advice; instead, the guidelines are provided for general informational purposes only. The guidelines contain links and references to third-party websites which are provided for the convenience of the reader and are not expressly endorsed by Dartmouth College.